Spyware VS Spy Software – What is the Difference? 2026
What’s the difference between spyware and spy software? It’s important to keep your computer safe, but all the tech terms can be confusing. While both involve spying, they’re not the same. Spyware is often harmful and can track your activity without your knowledge, while spy software is usually used for legitimate purposes, like monitoring kids or employees. In this article, we’ll break down what each term means and how they differ.
What Is Spyware?

Spyware is a type of software that gathers information about you without your knowledge. It often gets installed along with other programs, sneaking onto your computer without you noticing. Once it’s on your system, spyware tracks your online activities and personal information, sending that data to its creators, who may sell it to marketers. Unlike spyware, our spy software is designed for legitimate use, like keeping an eye on your kids or employees.
Characteristics of Spyware:
- Malicious Intent: Spyware is created with the intent to invade privacy and cause harm. It runs secretly without the user’s knowledge.
- Unauthorized Data Collection: It gathers information without the user’s permission, often breaching privacy laws and ethical standards.
- Stealth Operation: Spyware is designed to remain hidden from the user, making it difficult to detect and remove.
- Potential Harm: Beyond invading privacy, spyware can lead to financial loss, identity theft, and other forms of cybercrime.
What Is Spy Software?

Computer monitoring software, often called spy software, is made to track everything happening on a user’s computer. Unlike spyware, which can sneak in unnoticed, spy software is installed intentionally by someone who wants to monitor activity. You can easily purchase and set it up yourself. This software can either let users know they’re being monitored or run silently in the background. It captures almost every detail of computer use, and all the information is kept private, accessible only to the person who bought the software.
Characteristics of Spy Software:
- Varied Intent: Spy software can be used for both legitimate and questionable purposes. It might be employed to track a child’s online activity, monitor employee productivity, or secure a network from unauthorized access.
- Consent-Based: Ethical spy software often requires user consent or is used in environments where monitoring is legal.
- Transparency: Unlike spyware, legitimate spy software typically provides clear information about its monitoring activities and may include features for users to review the collected data.
- Legal Usage: Spy software can help effectively maintain security resources when used in compliance with laws. However, its use must always respect privacy and legal boundaries.
What Is The Difference Between Spyware And Spy Software
Understanding the distinction between spyware and spy software is crucial for both protecting oneself from malicious threats and using monitoring tools responsibly. Here’s a more detailed look at the key differences:
1. Purpose and Intent
Spyware:
- Malicious Intent: The primary purpose of spyware is to collect private information without the user’s consent. It is often used for illegal activities such as stealing sensitive data for identity theft, financial fraud, or unauthorized advertising. Spyware can also be used to gather competitive intelligence in a corporate environment, which, while not illegal in itself, is unethical and can result in serious consequences if discovered.
- Examples: Keyloggers record every keystroke, data harvesters steal personal information, and adware tracks browsing habits for targeted advertising.
Spy Software:
- Varied Intent: Spy software includes a variety of applications and has many uses; some are used to ensure security, and some are used to monitor employee productivity or keep children safe online.
- Examples: Parental control software that monitors children’s internet usage, employee monitoring tools that track your employees’ productivity and ensure they compliance with company policies, and security software that detects all unauthorized access attempts.
2. Consent and Transparency
Spyware:
- Lack of Consent: Spyware works without the user’s knowledge or consent. It often infiltrates systems through deceptive means, such as phishing attacks or bundled software installations, making it difficult for users to detect its presence.
- Opacity: Users are usually unaware that spyware is running on their systems. It operates stealthily, aiming to avoid detection and maintain its presence for as long as possible.
Spy Software:
- Consent-Based: Ethical spy software typically requires the user’s consent. For instance, employee monitoring software usually informs employees that their activities are tracked. Similarly, parental control applications require acknowledgment from both parents and children.
- Transparency: Legitimate spy software often includes features that allow users to review the data collected. For instance, security monitoring tools might offer dashboards showing recent activities, giving users visibility into how their data is used.
3. Legal Implications
Spyware:
- Illegal Activities: Due to its invasive nature, spyware is often illegal. Many countries have stringent laws prohibiting the unauthorized collection of personal information, and spyware frequently violates these laws. Engaging in spyware activities can lead to criminal charges, legal penalties, and civil lawsuits.
- Regulatory Oversight: Various regulations, such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the U.S., have specific provisions that outlaw the use of spyware and mandate strict data protection measures.
Spy Software:
- Legal Usage: Spy software can be completely legal when used within the bounds of the law. For example, companies can monitor employees if they comply with employment laws. Similarly, parents can monitor their children’s online activities with knowledge and consent.
- Compliance and Best Practices: The legal use of spy software usually requires compliance with relevant laws and regulations. This includes obtaining consent from those being monitored, providing transparency, and ensuring that data collection is limited to what is necessary for the intended purpose.
4. Detection and Removal
Spyware:
- Hard to Detect: Spyware is designed to be stealthy, and various techniques are used to avoid detection by standard antivirus and antimalware tools. It often hides within legitimate software or disguises itself to blend in with system processes, making it challenging for users to identify and remove.
- Complex Removal: Removing spyware typically requires specialized tools and expertise. Users might need to use advanced antivirus programs, perform manual scans, or seek professional assistance to fully eradicate spyware from their systems.
Spy Software:
- Manageable Detection: Legitimate spy software is often detectable through system settings or installed application lists. Users can usually find and review installed monitoring applications, and legitimate software often includes user interfaces that allow for easy configuration and management.
- Clear Removal Options: Most ethical spy software provides clear options for disabling or uninstalling the application. Users can typically remove the software through standard uninstallation procedures or adjust settings to limit its functionality.
Keep Online Safe With iKeyMonitor Best Spy Software?
iKeyMonitor stands out as the best spy software for both Android and iPhone devices. This powerful monitoring app offers comprehensive features designed to keep track of all online activities. With iKeyMonitor, you can easily monitor text messages, phone calls, websites visited, and photos. Additionally, the app provides advanced capabilities such as capturing screenshots, managing screen time, and listening to phone surroundings to protect your children from online threats, such as cyberbullying, sexual exploitation, online scams, and more. The following are key features of iKeyMonitor
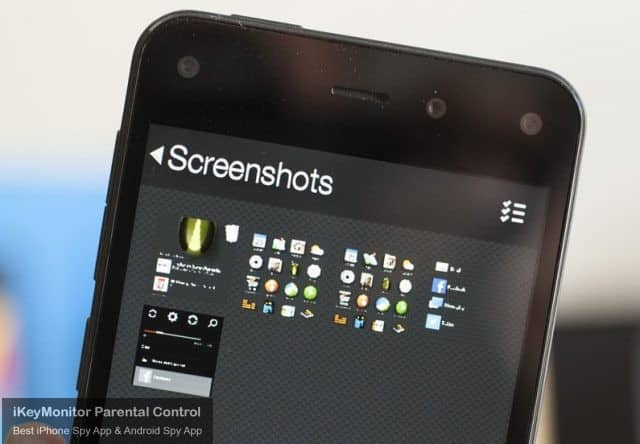
Capture Screenshots to Detect Suspicious Photos
iKeyMonitor regularly captures screenshots of online activities on the target Android phones and iPhone. You can log in to the cloud panel to check if there are suspicious photos.
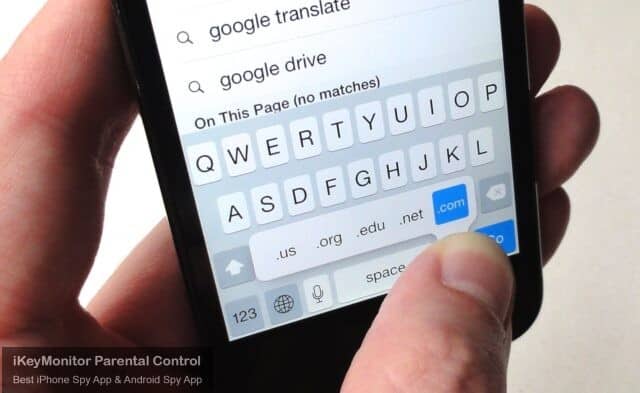
Track Keystrokes to Know Everything Typed
iKeyMonitor automatically tracks every keystroke typed in the background. You can view these keystrokes to know everything that happened.
Get Alerted about Dangerous Activities
iKeyMonitor allows you to add multiple alert words on your online cloud panel. Once the keywords are triggered, you will get instant alerts.
Conclusion
Understanding the difference between spyware and spy software is important for protecting your data. Spyware is harmful software that secretly gathers your personal information without your permission, which can lead to privacy issues and financial problems. On the other hand, the user installs spy software for good reasons, like keeping an eye on kids’ online activities or checking employee productivity. If you’re looking for a trustworthy and ethical monitoring option, iKeyMonitor is a great choice. It offers solid features for tracking text messages, calls, websites, and more.

Tags: computer monitoring software, employee monitoring, spy software, spyware
Category: Employee Monitoring Tips