How to Protect Your Children from Phishing Scams 2026
How to protect your children from phishing scams? Nowadays, threats such as phishing are all over the Internet world. As the use of social media and smartphones increases, this type of attack is increasing. To ensure your kids’ online safety, you need to protect them from phishing scams. Check out the guide below to learn how to identify and avoid phishing scams.
What Are Phishing Scams?
Phishing scams are attempts by scammers to trick you into giving out your personal information such as bank account numbers, passwords, and credit card numbers. If you can spot phishing scams in time, you can easily help your kids stop them. Here are three types of phishing scams:
- Email Phishing Scams: Fraudulent emails that appear to come from individuals or companies known to the victims. Scammers attempt to illegally collect personal and/or financial information from the recipient.
- Pop Up Warning Scams: When someone browses the Internet, a pop-up window will appear. This pop-up window may display a message stating that the computer is infected with malware and requires you to provide a phone number to help remove the malware.
- Fake Search Results Scams: Fraudulent companies spend money to place their ads on the top of the search results page. When you click on the ad, malware may begin to download to your device, thereby stealing your personal information or money.

4 Ways to Protect Your Kids from Phishing Scams
Here are four ways that you can take today to protect your kids from new phishing scams.
Setting Apps to Update Automatically
You can protect your children’s phones by setting the mobile apps to update automatically. These updates can provide children with critical protection against security threats. 
Use Multi-factor Authentication
You can protect your children’s accounts by using multi-factor authentication. Some accounts require two or more credentials to log in to the account, which provides additional security. If the scammer does get your children’s usernames and passwords, multi-factor authentication can make it harder for the scammer to log in to your children’s accounts.
Back Up Your Children’s Data
Protect your children’s data with backups. You can copy computer files to an external hard drive or cloud storage. Back up the data on your children’s phones.

Install A Parental Control App
You can use a parental control app like iKeyMonitor to protect your children. Download and install iKeyMonitor on your children’s mobile phones so that it can help you deal with any new security threats.
Recognize and Avoid Phishing Scams with iKeyMonitor
iKeyMonitor is specially designed for tracking the online activities on your children’s phones. It offers multiple features that help you recognize and avoid phishing scams. Here are some key features of iKeyMonitor:
Spy on Email to Detect Suspicious Emails
iKeyMonitor monitors emails by capturing screenshots of emails and recording the keystrokes typed in the emails on your children’s phones. Therefore, you can easily detect phishing scams and protect your children.

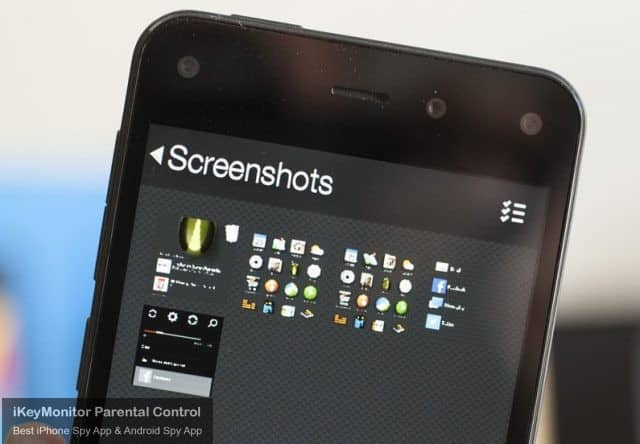
Capture Screenshots to Detect Suspicious Photos
iKeyMonitor regularly takes screenshots on your children’s phones. You can check the screenshot to see if your children have clicked on phishing emails.
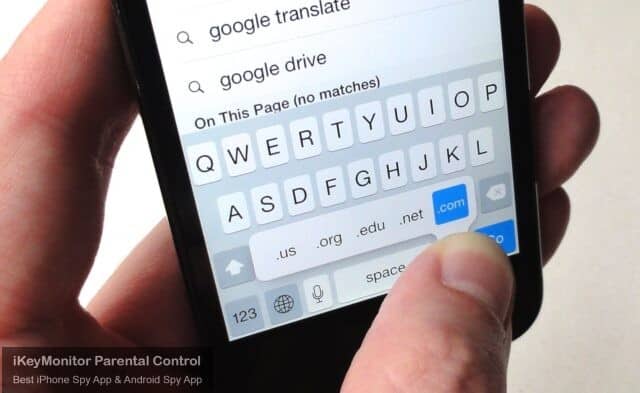
Track Keystrokes to Know Everything Typed
iKeyMonitor tracks every keystroke entered in your children’s smartphones. You can view the keystrokes to know if your children have leaked their personal information.
Get Alerted about Dangerous Activities
iKeyMonitor allows you to set keyword alerts on your children’s cell phones. You can set the words related to phishing scams as keywords so that you will get email alerts when these words are triggered.
Conclusion
If you are a parent who wants to protect your children from phishing scams, you can install iKeyMonitor on their device. After installing, you can remotely monitor your children’s online activities. The monitoring logs will be sent to you by email, after which you can find out if your children are in danger. Sign up and start protecting!

Tags: detect phishing scams, new phishing scams, phishing, phishing scams, spot phishing scams
Category: Learning & How to, Parental Control Tips