How to Spy on Mobile Phones Without Physical Access? 2026
Can You Spy On Mobile Phones Without Physical Access?
It sounds like something out of a spy movie to be able to spy on a cell phone without having physical access to it, but is it really possible? The answer is yes. There are several methods you can use to monitor someone’s phone without physical access, but they will have some limitations. Some specific methods are given later in this article.
How to Spy on Android Phones Without Access to Target Phone
Suppose you want to spy on an Android phone without physical access to the target phone; here are two methods you can try.
Using the backup account on the phone
If you want to track an Android phone without installing any software, you can check the backup account linked to that device. Most Android phones have built-in backup options that automatically save data to the cloud. By accessing this backup account, you can view important information like contacts, messages, and media files.
- Google Phone Backup
Google’s backup services primarily focus on ensuring your data is securely stored and restorable rather than providing a direct interface for users to view their backup content. However, here’s how you can restore data from a Google Backup:- Sign in with the Google Account associated with your backup when setting up a new Android device or after a factory reset on an existing device.
- During the setup process, the system will ask if you want to restore your apps and data from a previous device or backup. Choose the appropriate option.
- Select the one you wish to restore from if multiple backups are available.
- Follow the on-screen instructions to complete the setup. Your apps and data from the selected backup will be restored.
- Xiaomi Phone Backup
Here’s a general guide on how to view records via a Xiaomi backup account:- When setting up a new Xiaomi device or after a factory reset on an existing device, sign in with the Mi Account associated with your Mi Cloud backup.
- During the setup process, you’ll be prompted to restore your data from Mi Cloud. Choose the appropriate option.
- If multiple backups are available, select the one you wish to restore from.
- Follow the on-screen instructions to complete the setup. Your apps and data from the selected backup will be restored.
- Samsung Phone Backup
Samsung provides backup services primarily through Samsung Cloud or Google Account, depending on the device and region. If you have used Samsung Cloud for backup, here’s a general guide on how to view records via a Samsung Cloud account:- When setting up a new Samsung device or after a factory reset on an existing device, sign in with the Samsung Account associated with your Samsung Cloud backup.
- During the setup process, you’ll be prompted to restore your data from Samsung Cloud. Choose the appropriate option.
- If multiple backups are available, select the one you wish to restore from.
- Follow the on-screen instructions to complete the setup. Your apps and data from the selected backup will be restored.
CONS:
Using the backup account on an Android phone for monitoring requires account credentials, and very little information is available. For example, you can only view SMS, call history, contacts, calendars, etc., but you cannot view important things such as chat messages.
PROS:
Spy on the phone without physical access
Using router: spy on the phone without physical access through the same WiFi
You could monitor the device without physical access if you shared the same WiFi network as the target phone. It’s crucial to recognize that monitoring someone’s phone without their permission is unethical and illegal. Nonetheless, there might be instances where it becomes necessary, like keeping tabs on your employees’ activities on a company-owned device.
You can monitor the device without physical access if you’re connected to the same WiFi network as the target phone. However, it’s important to understand that checking someone’s phone without their permission is both unethical and illegal. There may be situations, like monitoring your employees on a company phone, where it might be necessary, but always ensure you’re following the law and respecting privacy.
- Monitor websites visited:
Monitoring websites visited through a router typically involves accessing the router’s administration interface or using specialized monitoring software. Some routers have built-in log-in or monitoring features. Look for sections like “Logs,” “Traffic Monitoring,” or “Parental Controls” in the router settings. They might display basic information about visited websites or domain names. - Monitor app usage:
The router cannot typically track detailed app-specific usage on devices connected to the network. However, some routers do log basic traffic information, which identifies the data usage of each connected device. This information is generally not provided by the apps that consume the data. You may consider using third-party software or applications designed to monitor network traffic, including OpenWRT Firmware with network add-ons, PFSense, NetFlow Analyzer, etc. - Monitor form data:
Some Man-In-the-middle tools such as Burp Suite, mitmproxy allow you to intercept and modify the web traffic between your browser and the server. You may use Burp Suite to read HTTPS form data such as passwords, usernames, web chat messages, etc.
CONS:
Spying on the phone without physical access through the same WiFi requires certain network management skills, so it may not be very user-friendly for novices.
PROS:
It is not necessary to physically access the target phone.
How to Spy on an iPhone Without Installing a Spying App
Spying on an iPhone without physical access may seem like a challenging task, but it is indeed possible. Below are two commonly used methods to monitor iPhone activity.
Using iPhone iCloud service
The iPhone iCloud service allows you to spy on the target iPhone without physically accessing it if you have its Apple ID and password. Logging into iCloud with the provided credentials, you can access a wide range of information, including messages, call logs, and even iPhone locations.
Using Find My iPhone: Spy on Phone Without the Target Phone
Another method to spy on an iPhone without installing a spy app is by using the Find My iPhone feature. This feature allows you to track the location of the phone, erase its data remotely, and even play a sound on the device to locate it. While this method doesn’t provide access to all the data on the phone, it can be helpful in certain situations.
How Can Hackers Spy On a Mobile Phone Without Physical Access?
While it’s important to protect your phone from unauthorized access, it’s also crucial to be aware of the methods hackers can use to spy on a mobile phone without physical access. Here are two common techniques used by hackers:
Phishing Attacks
Phishing attacks involve tricking the target into revealing sensitive information, such as login credentials or personal data. Hackers may send phishing emails or text messages that appear to be from a legitimate source, prompting the target to click on a malicious link or provide their information willingly.
Malware and Spyware
Your phone can be infected with malware and spyware without you realizing it. Once they have access, they can record your keystrokes, store data, and even control your phone remotely. Keeping your phone’s operating system and apps up-to-date and avoiding downloading apps from unknown sources will minimize the risk of your phone becoming infected with malware.
How to Stop Someone From Accessing Your Phone Remotely
Knowing the technology behind spying on a phone without physical access, you may wonder if your phone is being monitored. If you suspect someone has unauthorized access to your phone remotely, there are steps you can take to prevent further access and enhance your device’s security.
- Set a strong passcode or use biometric authentication methods such as fingerprint or face recognition.
- Enable two-factor authentication for your accounts to add an extra layer of security.
- Regularly update your phone’s operating system and apps to ensure you have the latest security patches.
- Be cautious when downloading apps and only use official app stores.
- Avoid clicking on suspicious links or opening attachments from unknown sources.
- Install reputable antivirus software on your phone to detect and remove any potential malware.
Using iKeyMonitor to Spy on A Mobile Phone With Physical Access
Suppose you have physical access to the target phone. In that case, there are many powerful monitoring apps that allow you to spy on mobile phones without physical access more freely, such as iKeyMonitor. iKeyMonitor is one of the most popular parental control applications. It can be used to monitor mobile phones without being detected. Unlike most cell phone spy software that only tracks locations, iKeyMonitor spy app contains all the advanced features necessary to truly get the answers you need.
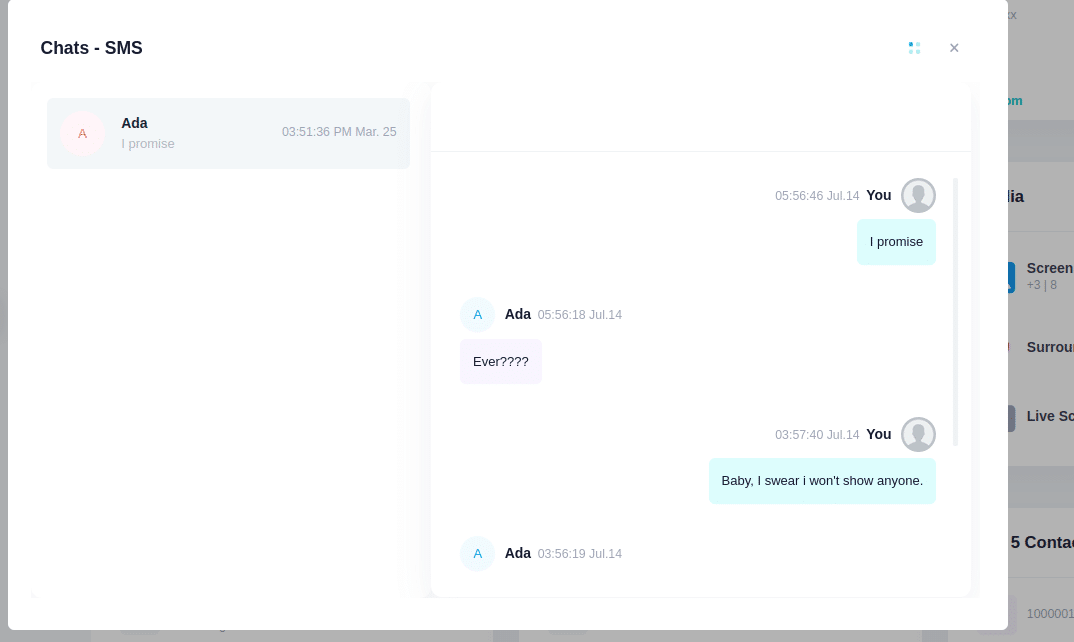
Spy on SMS Text Messages
iKeyMonitor monitors SMS text messages on target iPhone and Android phones, including SMS chat history, message content, date and time stamp, sender, and receiver. You can also recover deleted SMS text messages.
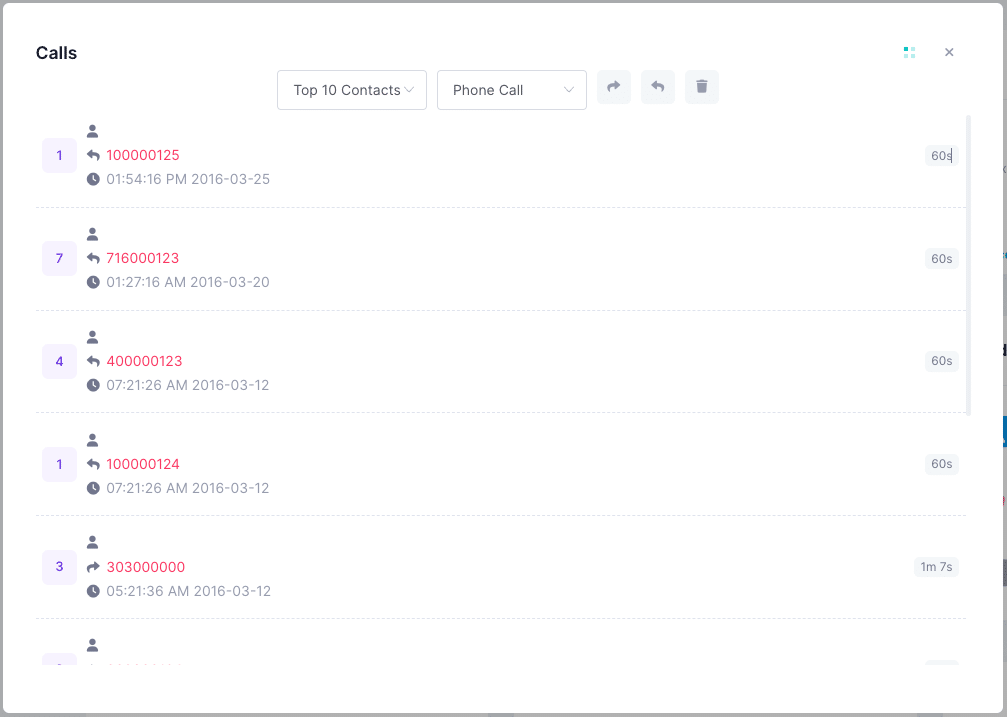
Monitor Call History
iKeyMonitor tracks the call logs on iOS and Android devices, providing you with detailed information on all incoming and outgoing calls. You can view the call history remotely to know who your child or employee is contacting, thus avoiding potential danger or trouble.
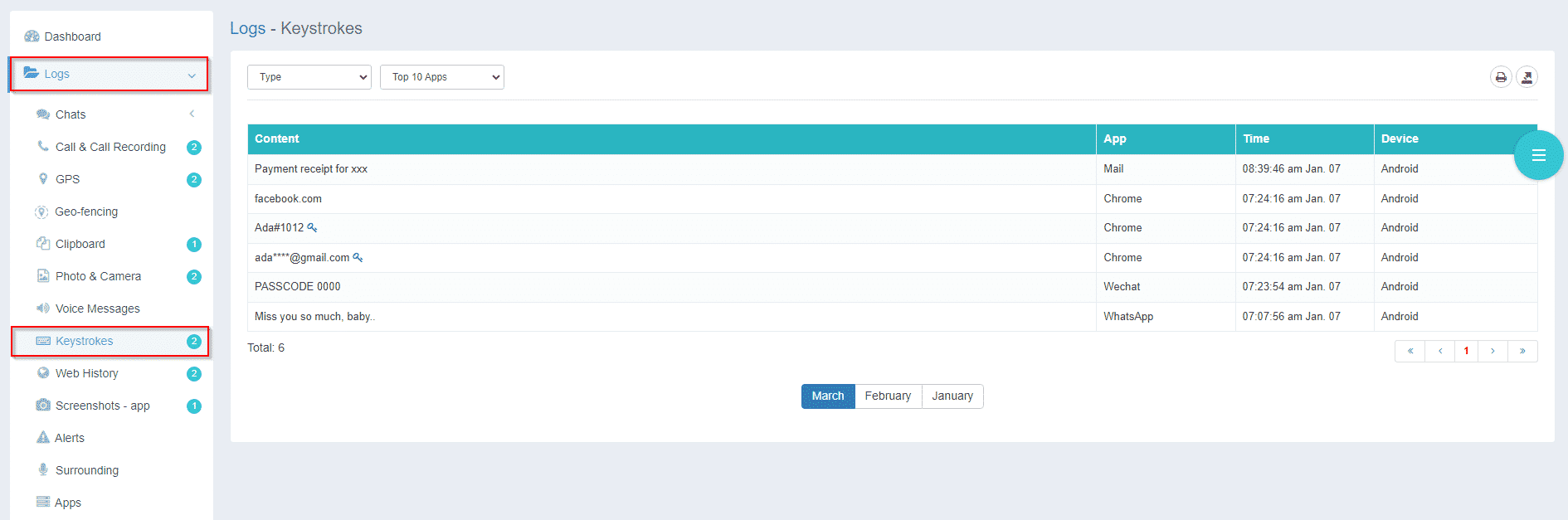
Record Keystrokes
iKeyMonitor Keylogger records all keystrokes typed on target iOS and Android devices, including pasted text in all applications, so you can clearly know what happened on the target device.
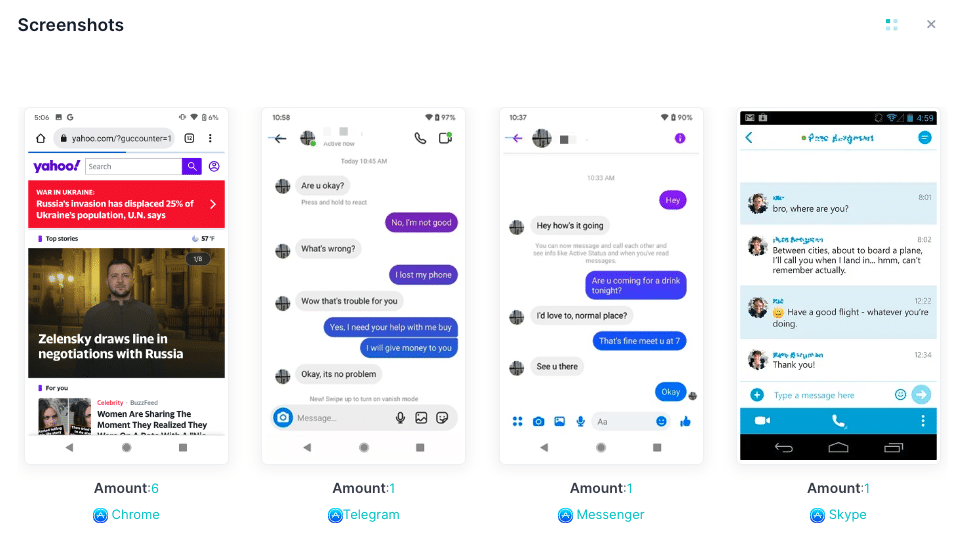
Take Screenshots
iKeyMonitor regularly takes screenshots of mobile activities, including photos, videos, chat applications, and visited websites, and you can check the activities performed on the target device. It can also capture screenshots of touch operations or when warning words are detected in keystrokes or application names.
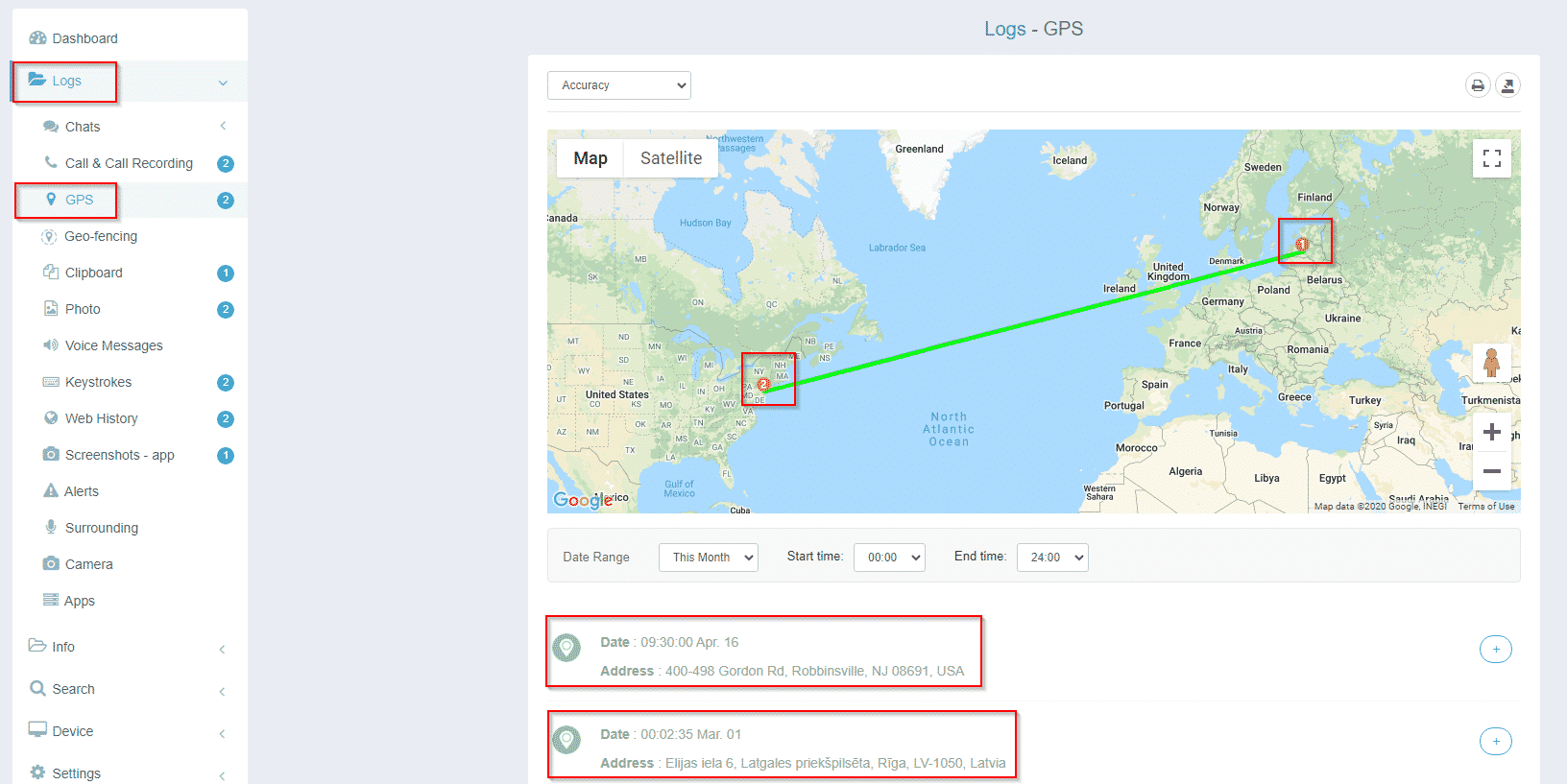
GPS Tracking
iKeyMontior tracks the GPS location of the target device at preset intervals so you can clearly know where your child has been or is currently. Apart from this, it also helps in recovering lost iPhones and Android devices by locating the location of the target phone.
Limit Screen Time
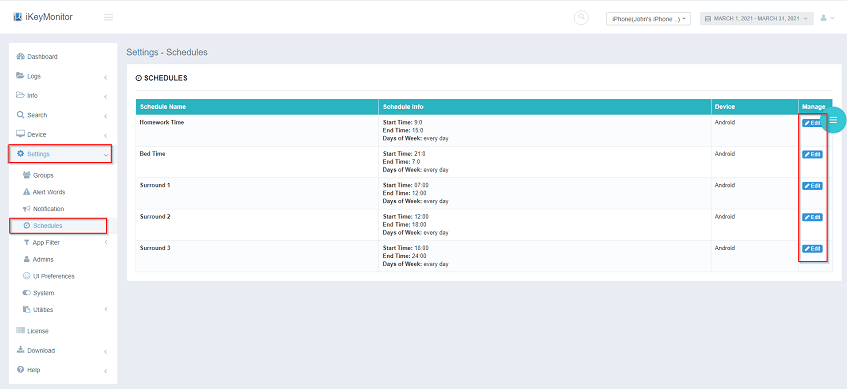
iKeyMonitor limits the screen time of iPhone/iPad/Android phones/tablets. This feature allows you to limit the time your children spend on mobile phones to keep them away from smartphone addiction.
Conclusion
In general, you can spy on a phone without physical access by using the iCloud service on an iPhone or checking the backup account linked to the device, but these methods have limits. If you can access the phone directly, parental control apps like iKeyMonitor can track calls, messages, GPS locations, and more. Just remember to always monitor phones ethically and legally by getting the necessary consent when needed.

Tags: mobile phone spy software, mobile spy software, phone monitoring, physical access, remote installation, remote spy, remote spy software, Spy on the Mobile Phone without Physical Access, spy software
Category: Learning & How to