How to Spy on Employees’ Computers? 2026
Spying on employees’ computers is crucial, especially when their tasks rely heavily on computers and the Internet. Without proper monitoring, these resources can easily be misused. An employee activity monitor helps employers track computer usage, ensuring productivity while maintaining a healthy level of trust with the team.
Why Need to Spy on Employees’ Computers?
Monitoring your employees’ computers is essential for keeping your business running smoothly. It’s not just about tracking their time; it’s about protecting your company’s data, ensuring productivity, and making sure your workplace rules are followed. Whether it’s preventing security issues, avoiding distractions, or ensuring compliance with company policies, keeping an eye on computer usage helps you run a more secure operation.
Increase Productivity
Tracking employee computer activity helps ensure that employees are staying focused on their tasks and not wasting time on non-work-related activities like social media or gaming. By identifying distractions, employers can intervene to help workers stay on track and be more efficient, ultimately leading to increased productivity and better results.
Employers report that 53% believe their companies lose 1-2 hours daily due to employee distractions, with personal device use being a major contributor.
Protect Company Data
By monitoring computer usage, employers can identify potential risks, such as employees accessing unauthorized files or visiting unsafe websites. This proactive approach helps safeguard confidential information, ensuring that company data remains secure from cyber threats, data theft, or accidental leaks.
Since 2021, there’s been a 28% average increase in monthly insider-driven data exposure, loss, leak, and theft events.
Ensure Company Policies Are Followed
By monitoring employee computers, employers can ensure that employees are adhering to these policies, whether it’s refraining from visiting inappropriate websites, protecting company intellectual property, or following email and communication guidelines.
How to Spy on Employees’ Computers Using iKeyMonitor?
If you’re an employer looking to keep track of how your employees use company computers, iKeyMonitor is a great option. It lets you monitor what they’re doing, from which websites they visit to the apps they use and what they type. This guide will show you how to set up iKeyMonitor to help you keep track of your employees’ computers, protect company data, and ensure your team stays focused on their tasks.
- Sign up for a free account of iKeyMonitor.
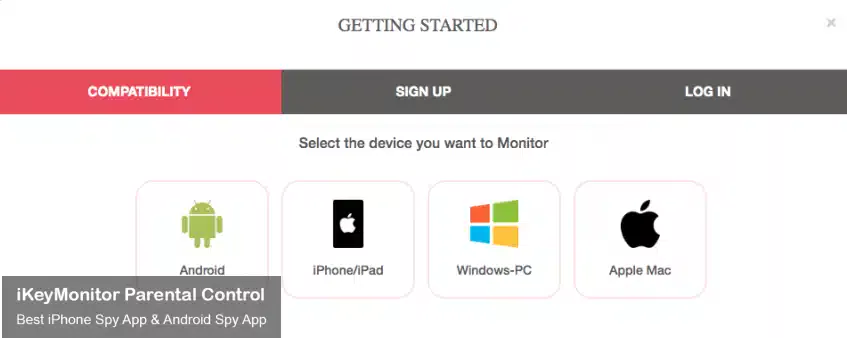
- Log in to the Cloud Panel and download iKeyMonitor to the target device.
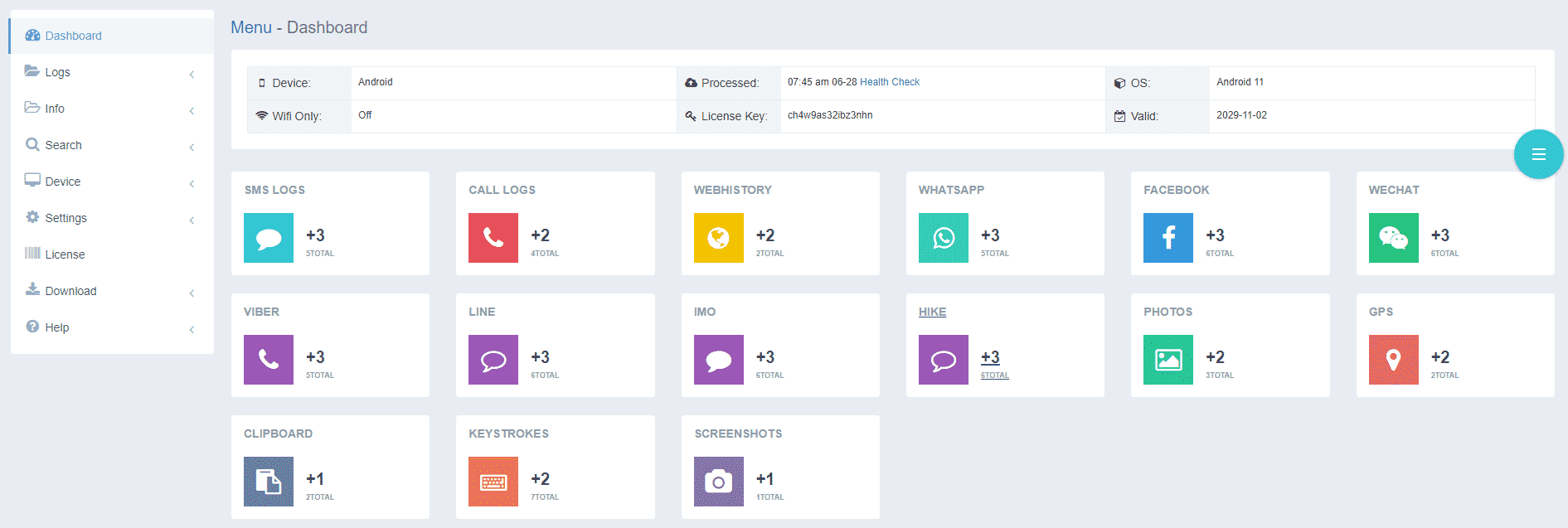
- Install iKeyMonitor and register it with your license key.
- Then, you can go to Logs to check all monitored logs.
Monitor Employees’ Computers to Improve Productivity with iKeyMonitor
iKeyMonitor is a simple tool for tracking employee activity on company computers. It helps you monitor keystrokes, web browsing, and social media use while allowing you to set screen time limits and block distracting sites. You can also track emails and overall efficiency. Using iKeyMonitor ensures employees stay focused and productive, protects company data, and keeps work hours used wisely.
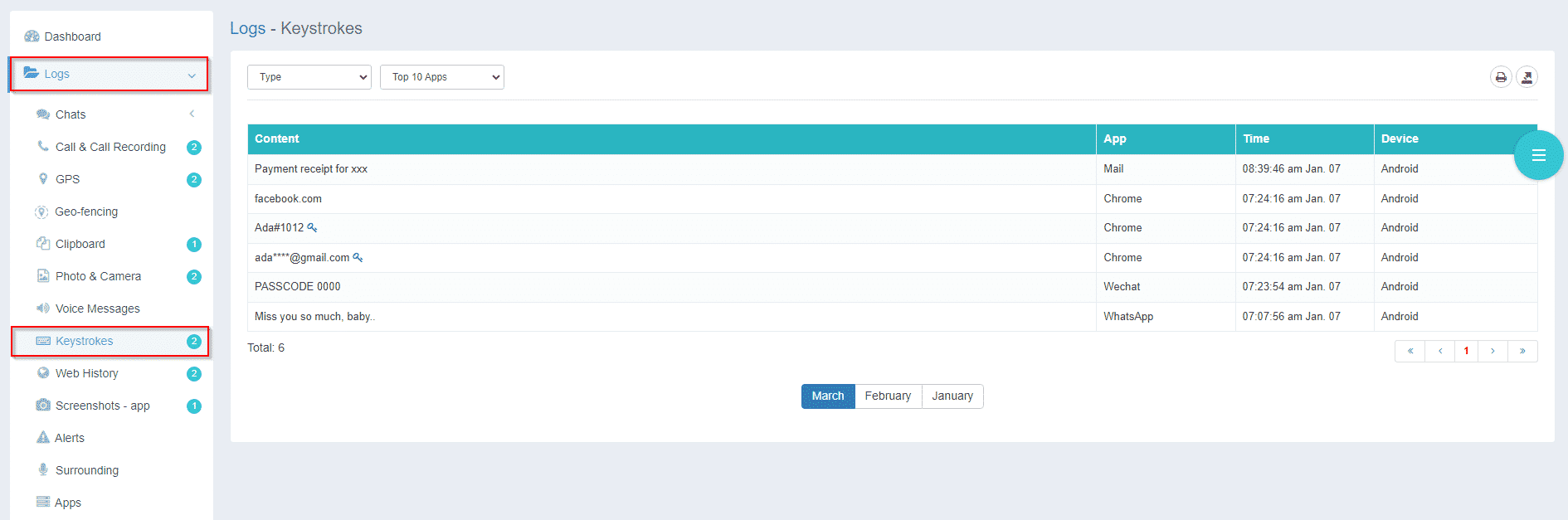
Track Every Keystroke for Better Insight
iKeyMonitor tracks every keystroke on your employees’ computers. This gives you a clear idea of what they’re working on, what applications they use, and whether they are staying on task. It’s a simple but effective way to catch any issues early, especially when it comes to sensitive data or unauthorized software use.
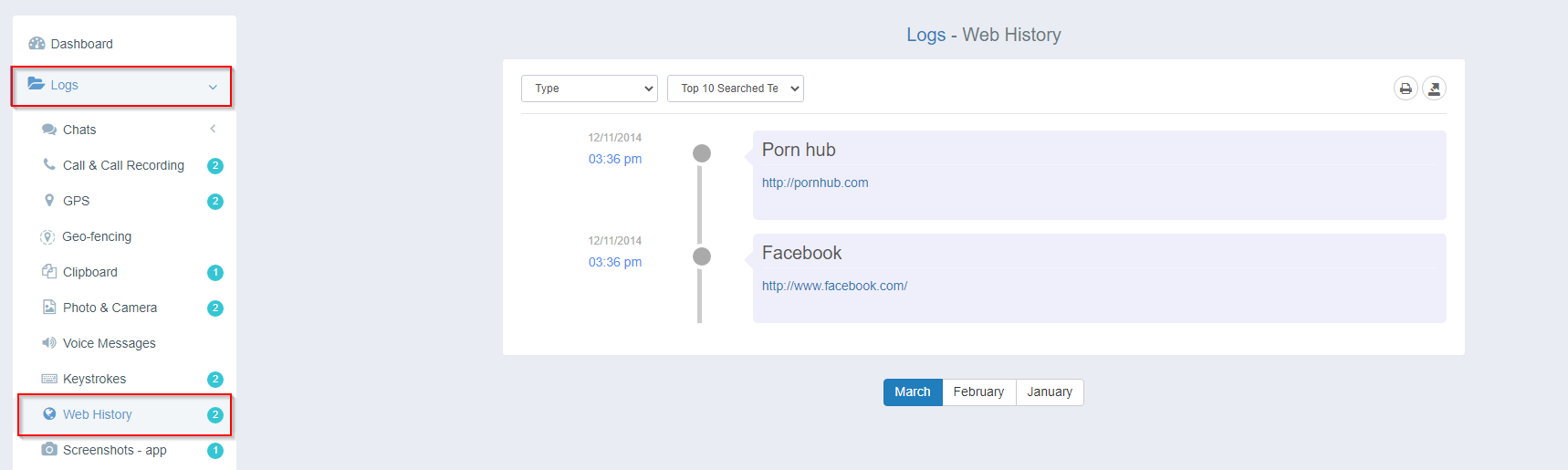
Monitor Web Browsing to Prevent Distractions
Use iKeyMonitor to monitor your employees’ browsing history. You’ll have a clear view of the websites they visit, allowing you to spot any time wasted on non-work-related sites, such as social media, entertainment, or shopping.
Set Screen Time Limits for Better Work-Life Balance
Too much screen time can hurt productivity and focus. iKeyMonitor lets you set daily screen time limits for employees, encouraging them to take breaks and maintain better work-life balance, which ultimately improves their efficiency.
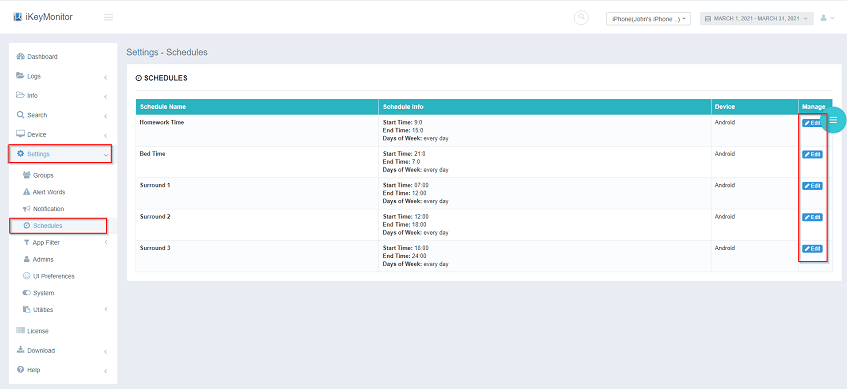
Block Access to Disruptive Websites
With iKeyMonitor, you can block access to websites that are not work-related or pose security threats. This helps employees stay focused on the task at hand while preventing access to harmful or distracting content.

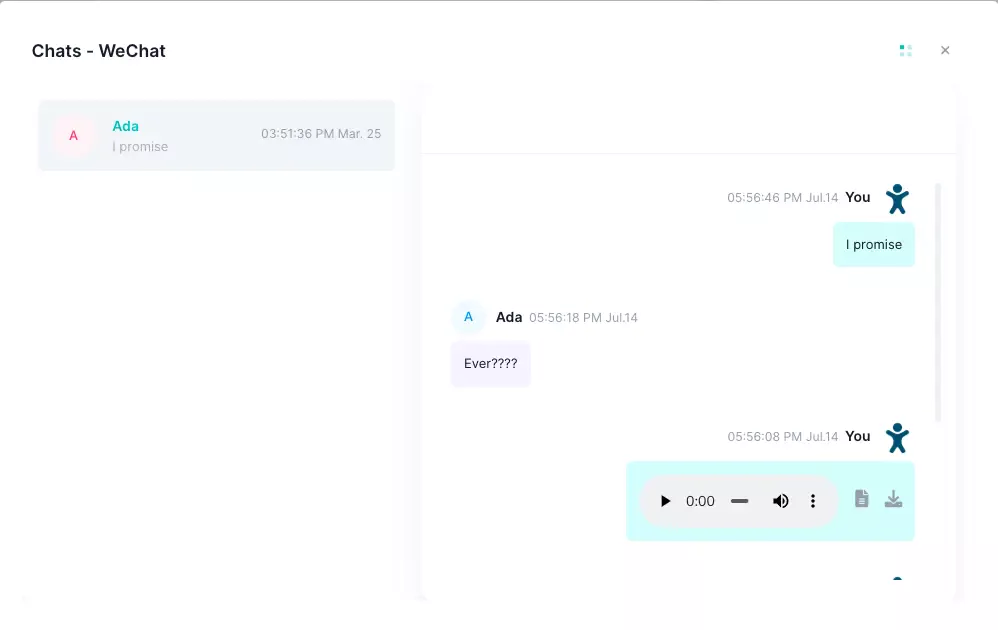
Keep Track of Social Media Chats for Better Oversight
It’s easy for employees to get caught up in personal chats during work hours. iKeyMonitor allows you to monitor communication on platforms like WhatsApp, Facebook Messenger, and more. This ensures that employees are using company time for work, not personal conversations.
Monitor Email Communications to Protect Company Data
Email is one of the primary ways employees communicate at work, but it’s also an easy way to send sensitive or personal messages. With iKeyMonitor, you can keep track of all sent and received emails, so you know your company’s data is secure and being handled responsibly.

FAQs About Spying on Employees’ Computers
Q1. Is it legal to spy on employees’ computers?
Yes, as long as it complies with local laws and workplace policies. Employers should inform employees about monitoring. Using tools like iKeyMonitor ensures transparency and legal compliance.
Q2. How can I monitor employees’ computer activities?
You can monitor employees using software like iKeyMonitor. It tracks keystrokes, web browsing history, social media activity, and more, helping employers ensure productivity and security.
Q3. Can I block websites on employees’ computers?
Yes, iKeyMonitor allows employers to block distracting websites and apps during work hours, ensuring employees stay focused on tasks that matter.
Q4. How can I track employee productivity remotely?
iKeyMonitor provides features like keystroke logging, screen monitoring, and web history tracking, helping you keep track of employee productivity, even remotely.
Q5. What is the best software for monitoring employee computer usage?
iKeyMonitor is an excellent employee monitoring software. It offers a variety of tracking features, including activity logging, social media monitoring, screen time restrictions, and more, to boost workplace productivity.
Q6. Can I monitor employees’ social media activity?
Yes, iKeyMonitor allows you to track social media activity on apps like Facebook, WhatsApp, and Instagram, helping employers ensure employees aren’t wasting work time on personal tasks.
Conclusion
Tags: computer spy software, employee activity monitor, employee computer monitoring, employee monitoring software, Spy on employees computers
Category: Employee Monitoring Tips