Hardware Keylogger vs Software Keylogger: What They Are and How to Protect Yourself 2024
Do you know about hardware keyloggers and software keyloggers? These tools record every keystroke on a computer without the user knowing. They can automatically track all keyboard activity and are often used to monitor kids or employees. In this article, I’ll explain how hardware and software keyloggers work and how you can protect yourself from them.
What Is A Software Keylogger?
A software keylogger records everything you type on a computer or mobile device, including texts, passwords, and commands. It then sends this information to a remote server. People often use keyloggers to keep track of employee activity or to monitor their kids online.
Features:
- Logs can be sent to an email or FTP address for easy access.
- Some include website and application-blocking features.
- Can capture screenshots and track websites visited.
What Is A Hardware keylogger?
A hardware keylogger is a physical device that records everything typed on a computer or keyboard. It typically connects between the keyboard and the computer or is built into the keyboard. This device captures all keystrokes, including texts and passwords, and stores the data for later use. Unlike software keyloggers, hardware keyloggers work independently of the computer’s software, making them effective for monitoring without altering the system.
- Definition: These are physical devices installed between the keyboard plug and the motherboard socket, making them difficult to detect.
- Uses: Typically used when an attacker has physical access to the computer.
- Detection: It is difficult to detect without a physical review of the keyboard connection.
How to Use Software Keyloggers to Protect Your Network?
Want to keep your network safe and secure? Using a software keylogger app can be an effective way to monitor activity and detect suspicious behavior. The following will show you how to use software keyloggers effectively to safeguard your network from potential threats.
Installation:
- Bundled with Other Software: Some keyloggers come bundled with other legitimate software, installing themselves without the user’s knowledge when the primary software is installed.
- Direct Installation: Others require manual installation and may even need an admin password, making them visible to the person installing them.
Functionality:
- Keystroke Recording: The primary function is to log every keystroke on the keyboard.
- Additional Features: Advanced keyloggers can capture screenshots, track websites visited, log application usage, and send this data to a specified email or FTP server.
Usage:
- Parental Control: Parents can use keyloggers to monitor their children’s internet activities and ensure safe online behavior.
- Employee Monitoring: Employers can use them to monitor employees’ activities to ensure productivity and adherence to company policies.
Steps to Deploy Software Keyloggers:
- Selection: Choose keylogger software that meets your needs (e.g., parental control or employee monitoring).
- Download: Obtain software from a legitimate source to avoid malicious versions.
- Installation: Install the software on the target computer, following the instructions. This may require administrative access.
- Configuration: Configure the keylogger settings, specifying where logs should be sent (email, FTP) and what additional activities to monitor (screenshots, websites).
- Monitoring: Regularly check the keylogger logs to review the captured data.
- If required by law or ethical guidelines, ensure you have the legal right to monitor the computer.
How to Use Hardware Keyloggers to Keep Your Data Safe?
Looking to protect your data from unauthorized access? Hardware keylogger software can be a useful tool for securing your information. This guide will explain how to use hardware keyloggers to keep your data safe and help you avoid potential online threats.

Installation
- Physical Access: The installer must have physical access to the computer to insert the device between the keyboard’s plug and the computer’s port.
- Discreet Placement: The keylogger is often designed to blend in with the existing hardware, making it difficult to notice unless someone looks for it.
Functionality:
- Keystroke Recording: The device captures and stores all keystrokes on the keyboard.
- Data Retrieval: To access the recorded data, the device must be physically removed and connected to another computer. The data can then be downloaded and reviewed using specialized software that comes with the keylogger.
Usage:
- Surveillance: Used in scenarios where software keyloggers might be detected or where keystrokes need to be monitored without installing software.
- Security Testing: Used by security professionals to test and demonstrate vulnerabilities in a computer system.
Steps to Deploy Hardware Keyloggers:
- Selection: Choose a hardware keylogger that fits the type of keyboard connection (e.g., USB, PS/2).
- Installation: Physically connect the keylogger between the keyboard and the computer’s keyboard port.
- Configuration: Some advanced hardware keyloggers may require initial configuration using specialized software provided by the manufacturer.
- Monitoring: Let the keylogger run, capturing all keystrokes. Periodically, the device must be retrieved to access stored data.
- Data Retrieval: Disconnect the keylogger, connect it to another computer, and use the provided software to download and review the recorded keystrokes.
- Ethical Considerations
Using iKeyMonitor Software Keyloggers to Monitor Online Activities
Monitoring the target device’s online activities is essential to maintaining data security. As the best software keylogger, iKeyMonitor provides a powerful solution to track SMS, calls, web browsing history, GPS, and more. Here’s how you can use iKeyMonitor to keep data safe:
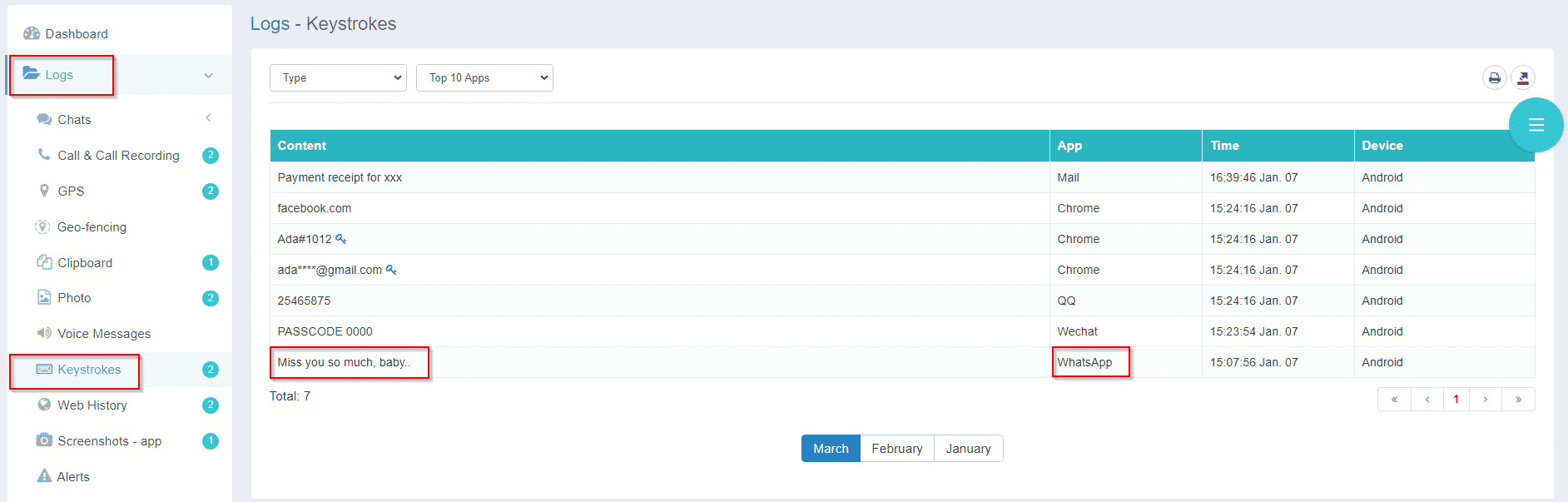
Track Typed Keystrokes
One of the primary features of iKeyMonitor is its ability to track every keystroke typed on a device. This means you can see exactly what is being entered into search engines, social media platforms, and other applications. By recording all typed text, iKeyMonitor helps you monitor communications, detect potential security risks, and understand user behavior. Whether you’re looking to monitor employee activity or ensure your children’s online safety, tracking keystrokes provides a detailed record of all written content.
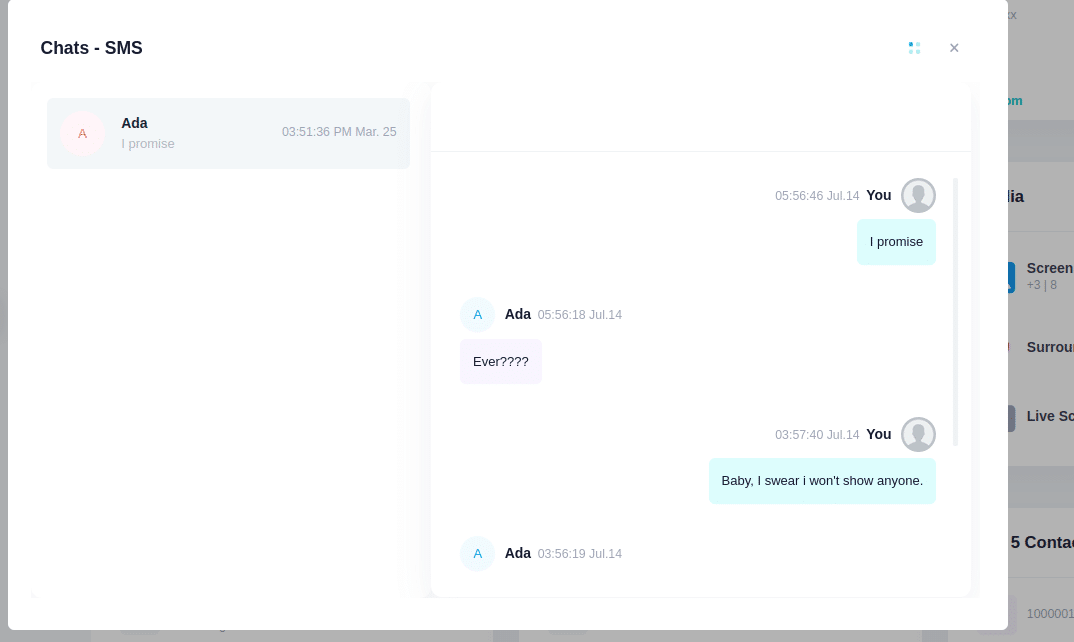
Monitor SMS Text Messages
iKeyMonitor also monitors SMS text messages sent and received on the target device. This feature is particularly useful for staying informed about the communications taking place via text. You can access a comprehensive log of SMS messages, including content, timestamps, and sender information.
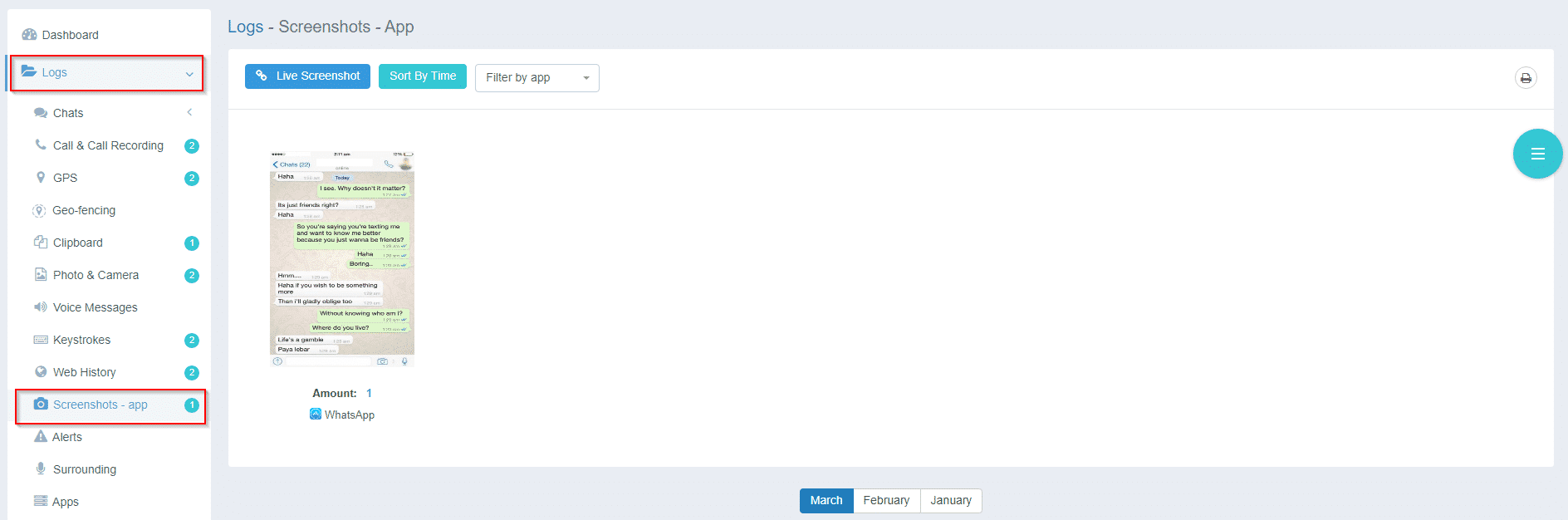
Capture Screenshots
Another valuable feature of iKeyMonitor is the ability to capture screenshots of the device’s screen. This function allows you to visually monitor what is being displayed in real-time, giving you insight into the user’s activity beyond just typed text. Regular or on-demand screenshots can reveal what websites are visited, which apps are used, and what content is being viewed.
Conclusion
Keyloggers can be used for good or bad reasons, so it’s important to take steps to protect your personal information. Make sure to use reliable hardware keyloggers and software keyloggers and keep them updated to help keep your data safe. Also, use strong and unique passwords, and turn on two-factor authentication to boost your account security. By staying informed and following these tips, you can lower the chances of falling victim to a keylogger and keep your sensitive information secure.

Tags: hardware keylogger, keylogger, Software keylogger
Category: Employee Monitoring Tips